Internet censorship circumvention describes various processes used by Internet users to bypass the technical aspects of Internet filtering and gain access to otherwise censored material. Circumvention is an inherent problem for those wishing to censor the Internet, because filtering and blocking do not remove content from the Internet and as long as there is at least one publicly accessible uncensored system, it will often be possible to gain access to otherwise censored material. However, circumvention may not be very useful to non-tech-savvy users and so blocking and filtering remain effective means of censoring the Internet for many users.
This document is intended to help users configure their computers to protect their privacy while browsing the web. Easy stuff is at the beginning, and harder stuff is toward the end. This howto guide is intended for a general audience, so wording is necessarily simplified. For the greatest benefit, use as many tools/methods as you can, in combination.
This site is meant to be a resource to those who value their privacy, specifically those looking for information on VPNs (that isn’t disguised advertising). There are some other good resources that cover privacy based topics quite well, but when I started down the path of retaking my own privacy, there was very little unbiased and reliable information with regard to VPNs.
2009-06-18
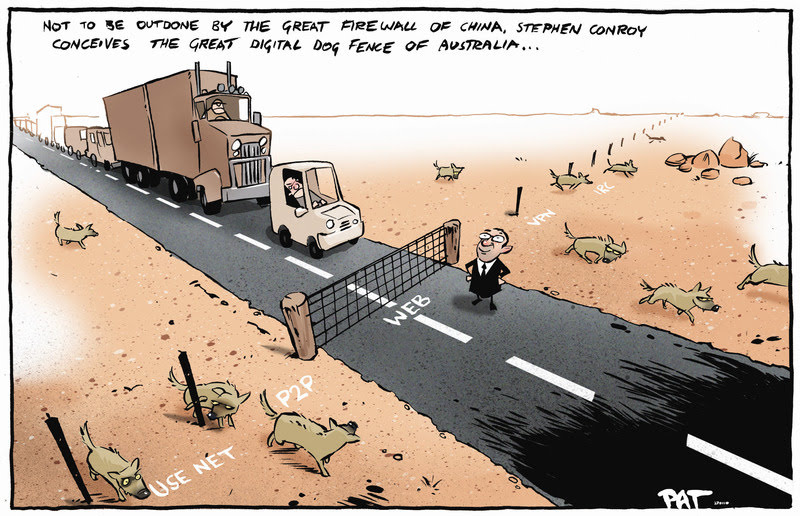
Today, Germany’s lower house passed the first Western national internet censorship law. As every news organization, political newsletter and discussion between friends relocates onto the internet, censorship systems are being rolled out to interpose themselves between every communicator and their audience.
We’re arresting you for speeding.
What’s the speed limit, officer?
The speed limit is secret.
“The Internet interprets censorship as damage and routes around it.” - John Gilmore
If your employer or corrupt, undemocratic, dictator-based government uses a filtering service such as Secure Computing’s SmartFilter to block access to BoingBoing.net—or anything else online—you can try the following workarounds.
This guide is meant to introduce non-technical users to Internet censorship circumvention technologies, and help them choose which of them best suits their circumstances and needs.
- source_1 (scroll down to Publications -> Guides)
- Burmese translation (PDF)
- Russian translation (PDF)
When [the Universal Declaration of Human Rights] were written sixty years ago, no one imagined how the global phenomenon of the Internet would expand people’s ability to “seek, receive and impart information”, not only across borders but at amazing speeds and in forms that can be copied, edited, manipulated, recombined and shared with small or large audiences in ways fundamentally different than the communications media available in 1948.
As more countries crack down on Internet use, people around the world are turning to anti-censorship software that lets them reach blocked websites. Many types of software, also known as circumvention tools, have been created to answer the threat to freedom online. These tools provide different features and levels of security, and it’s important for users to understand the tradeoffs. This article lays out ten features you should consider when evaluating a circumvention tool.
- China Rights Forum 2010, no. 2 - “China’s Internet”: Staking Digital Ground
- China Rights Forum 2010, no. 2 - “China’s Internet”: Staking Digital Ground (Chinese translation)
- source: Ten things to look for in a circumvention tool, linked from Tor Documentation Overview → Getting up to speed on Tor’s past, present, and future → i. Learn about our censorship circumvention side → …an overview of what to look for in a circumvention tool…
“Facilitating access to the Internet for all individuals…should be a priority for all States”